Example case
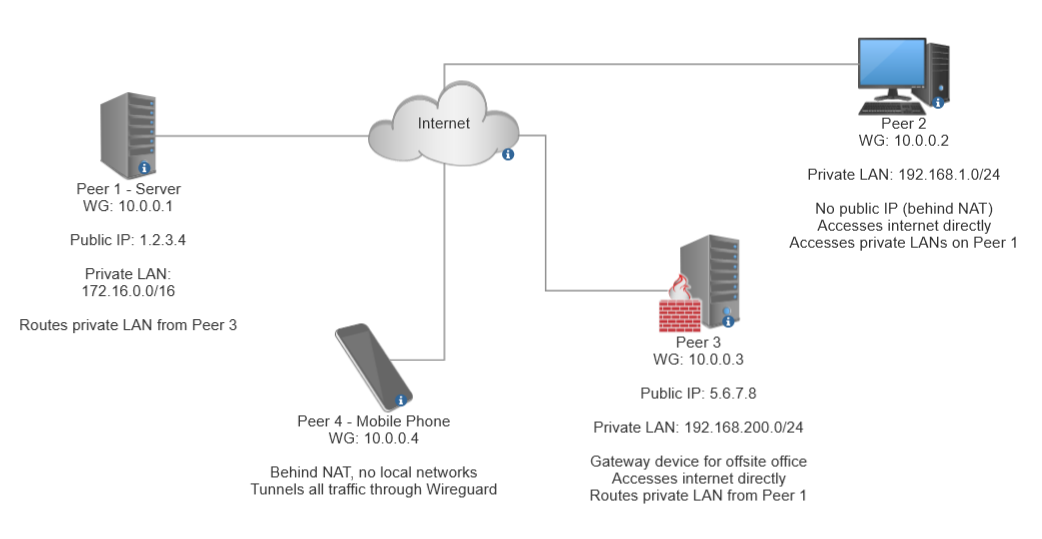
Consider the network setup below.
Peer 1 (server) is the central point (server) of the setup, accepting connections from the other peers and also tunnelling traffic from some of them. It has its interface configuration and knows the public keys and IPs of all other peers. Additionally, it knows the local networks for Peer 3, which is a bit special. Peer 2 and 3 can see each other (and the whole VPN IP address space) – reflected by the /24 netmask, while Peer 4 cannot (receives a single-host /32 netmask instead). Tunnelled peers also use the server (peer 1) as DNS resolver to avoid leaking out access information.
[Interface] Address = 10.0.0.1/24 ListenPort = 12345 PrivateKey = SERVER_PRIVATE_KEY # PublicKey = SERVER_PUBLIC_KEY PreUp = iptables -I INPUT -p udp --dport 12345 -j ACCEPT; iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADE PostDown = iptables -D INPUT -p udp --dport 12345 -j ACCEPT; iptables -t nat -D POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADE # regular PC [Peer] PublicKey = PEER1_PUBLIC_KEY PresharedKey = PEER1_PRESHARED_KEY AllowedIPs = 10.0.0.2/24 # remote office gateway/router - interconnected resources [Peer] PublicKey = PEER2_PUBLIC_KEY PresharedKey = PEER2_PRESHARED_KEY AllowedIPs = 10.0.0.3/24, 192.168.200.0/24 # portable device [Peer] PublicKey = PEER3_PUBLIC_KEY PresharedKey = PEER3_PRESHARED_KEY AllowedIPs = 10.0.0.4/32
Peer 2 is a generic computer (located anywhere), accesses the internet directly (is not tunneled) but also requires access to the server’s internal network resources – its AllowedIPs configuration reflects this.
[Interface] Address = 10.0.0.2/24 PrivateKey = PEER2_PRIVATE_KEY [Peer] Endpoint = 1.2.3.4:12345 PublicKey = PEER2_PUBLIC_KEY PresharedKey = PEER2_PRESHARED_KEY AllowedIPs = 10.0.0.0/24, 172.16.0.0/16
Peer 3 is a gateway/router for a remote office. It has access to the server’s own internal network (and shares this with its own internal network).
Additionally, the server (Peer 1) has access to the peer’s own internal network (the AllowedIPs line in the server’s configuration reflects this).
Also, all network traffic from this whole local network is tunneled through the WireGuard VPN. While its public IP address is known, that is irrelevant as no other peers initiate connections to this peer directly.
[Interface] Address = 10.0.0.3/24 PrivateKey = PEER3_PRIVATE_KEY DNS = 10.0.0.1, 1.2.3.4 [Peer] Endpoint = 1.2.3.4:12345 PublicKey = PEER3_PUBLIC_KEY PresharedKey = PEER3_PRESHARED_KEY AllowedIPs = 0.0.0.0/1, 128.0.0.0/1
Peer 4 is a portable device which doesn’t have access to any of the internal resources but needs to have all its traffic tunneled through the VPN.
[Interface] Address = 10.0.0.4/24 PrivateKey = PEER4_PRIVATE_KEY DNS = 10.0.0.1, 1.2.3.4 [Peer] Endpoint = 1.2.3.4:12345 PublicKey = PEER4_PUBLIC_KEY PresharedKey = PEER4_PRESHARED_KEY AllowedIPs = 0.0.0.0/0, ::/0